or Archive

What comes first, teamship or friendship?
Loknath Das
Comments off
When you think about a great team you have been in, do you think about the work, or do you think about

How To Post To Instagram From PC or Mac
Loknath Das
Comments off
Wondering how to post to Instagram from a PC or Mac computer? You’re in the right place… To the dismay of people

How to use your Android or iOS device as a webcam
Loknath Das
Comments off
A good webcam, let alone any webcam, is tough to find these days. Just to put a time marker on this post:

The 8 best Apple Arcade games for your new iPhone or iPad
Loknath Das
Comments off
The world of iPhone and iPad games changed dramatically in September with the launch of Apple Arcade. The subscription is an incredible

Whether it is The iPhone 4 or iPad Pro Inspiration, Next Apple iPhones Could have Flat Sides
Loknath Das
Comments off
While there is plenty of debate about the design of Apple’s latest iPhone 11 series, there are others who are thrilled with
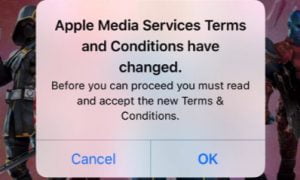
Bug in Apple’s iTunes and iOS App Store stopping some users from downloading or updating purchases [u]
Loknath Das
Comments off
An unknown number of users are currently unable to buy new apps or download updates because of a bug in Apple’s iOS

How to Reset Any iPhone or Android Device
Loknath Das
Comments off
You’re getting ready to sell or give away your iPhone, iPad, or Android device, but first you want to wipe all traces
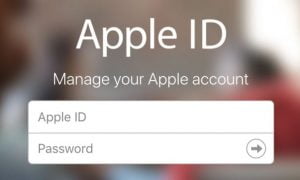
How to Change or Reset Your Apple ID Password
Loknath Das
Comments off
Your Apple ID account is used for so many things you can do with Apple devices and services, such as shop on

Do Business With Iran Or United States: Donald Trump Warns World
Loknath Das
Comments off
US President Donald Trump on Tuesday said that sanctions reimposed on Iran were the “most biting ever” as he warned other

Is boasting good or bad for business?
Loknath Das
Comments off
So is this humility a help or a hindrance when it comes to start-ups? From household names such as Spotify and Skype,
- 1
- 2