Software Archive

vivo teases S15 with official images
Loknath Das
Comments off
vivo posted press images of its upcoming S15 smartphone on Weibo, revealing its color options. The vivo S15, S15 Pro, and TWS Air earbuds
Understanding Microsoft’s Value Proposition in the US Software Space
Catherine Garcia
Comments off
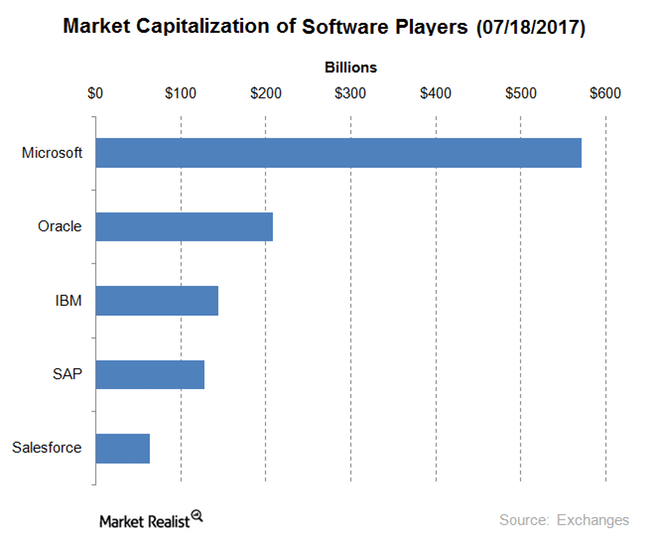
Microsoft’s scale in systems software Previously in this series, we discussed Microsoft’s technical indicators. Now, let’s look at its value proposition among

Pattern to trial predictive analytics software
Catherine Garcia
Comments off
Uptake claims its software can identify failures before they happen and make recommendations to increase uptime and productivity. The industrial data software

How to use Gmail’s Google Tasks as your daily to-do list
Catherine Garcia
Comments off
Dedicated to-do apps abound, but one of the best may be right in your inbox. Google Tasks, integrated into Gmail, provides a

The 6 Software Engineering Blogs You Should Read
Loknath Das
Comments off
Here are some of the most popular software bloggers, their subject matter, backgrounds and style of writing, and a summary of what

Must-Read Software Development Blogs
Loknath Das
Comments off
With new technologies flooding every day, it is hard to keep up with all the updates. Blogs are a valuable resource for
5 Best Responsive Web Design Practices In 2018
Loknath Das
Comments off
By now you may have heard the term “responsive web design” being thrown around. In case you’re new to this concept or
Why Video Formats Are Important – And What They Do?
Loknath Das
Comments off
Unless you have experience creating or editing videos, you probably have mostly ignored the format that your videos are in. In fact

New Software Provides an All-In-One Solution for CRE
Loknath Das
Comments off
Real Clear Software is launching a RCS Portfolio, a new software that will house data in a single place. Real estate is largely a

Why Use a VPN When Doing Public Web Browsing?
admin
Comments off
With the popularity of virtual private network or VPN on the rise, it was evident that it has many advantages that can